The LumenVox Dashboard is designed to operate using either HTTP or HTTPS connectivity, allowing remote access to the services running on each LumenVox server. It is important that only authorized users are able to access this functionality to prevent disabling or changing those services, so there is an optional username and password requirement that can be enabled. In addition to this, it is possible to use HTTPS, which is the secure form of the regular HTTP communications protocol. This secure mode utilizes SSL (Secure Sockets Layer) to encrypt this communication, so is preferred, preventing anyone intercepting username and passwords being sent as well as any other information passed over the communications channel in the form of eavesdropping or other tampering.
Note that if using HTTP as the communications protocol, certificates are not used, and therefore do not need to be configured when connecting to the Dashboard, however we encourage users to select HTTPS whenever practical.
SSL requires the use of a certificate that is installed on the web server, which identifies the server as well as providing information on the encryption mechanism to be used. See this HTTP_Securearticle for more details.
Since the Dashboard is being driven by a web server within the LumenVox manager service, this service needs a certificate in order to provide HTTPS connectivity. By default, LumenVox installs a dummy certificate, located in /etc/lumenvox/www/certs(on Linux) or C:\Program Files\LumenVox\Tools\www\certs (Windows) - this dummy file is called server.pem. Since this is a dummy file, the signature of the certificate will not match your server, or domain, which will (correctly) cause your browser to treat the Dashboard site with suspicion, since it cannot validate the authenticity of the certificate. This will be indicated by a warning in your browser:
Certificate Error:
Certificate Error generated by Internet Explorer when attempting to open Dashboard with default certificate
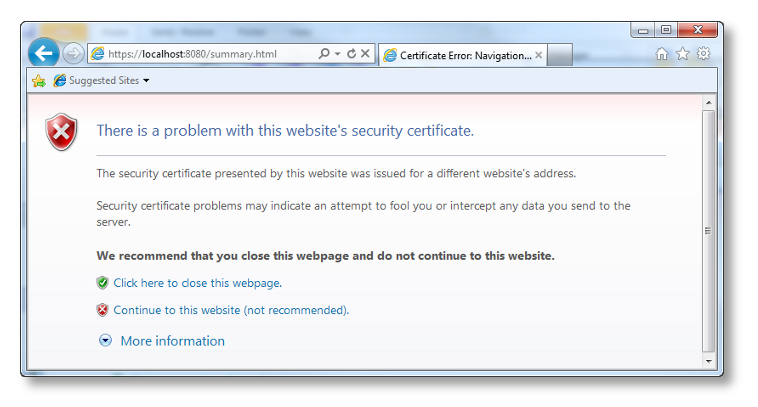
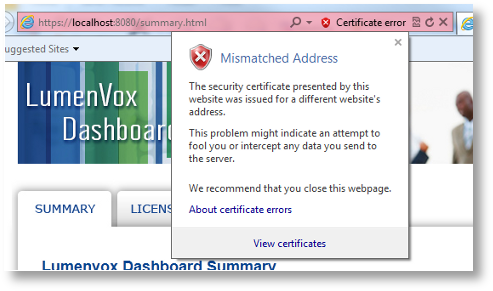
After continuing to the Dashboard, the browser will continue to indicate a problem with the certificate as shown here:
Details of Certificate Mismatch (Chrome):
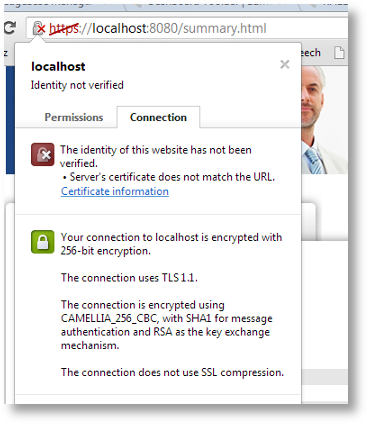
Details of Certificate Mismatch (Internet Explorer):
Resolution
To resolve these problems, you should install your own authentication certificate for the server, which can be obtained from a registered certificate authority, such as VeriSign or Go Daddy (there are many others).
After obtaining the certificate for the server, a compatible pem (Privacy Enhanced Mail) file needs to be saved to disk, and this new certificate file will need to be referenced and used by the LumenVox Manager. The name and location of this certificate (.pem) file can be specified in the manager.conf file. The Manager service will need to be restarted after this configuration setting is changed for it to take effect.
Please note that the above information is being made available here to assist our customers in generating certificate files, however LumenVox does not provide, configure or provide help with these. You need to contact one of the signing authorities to obtain these certificates.
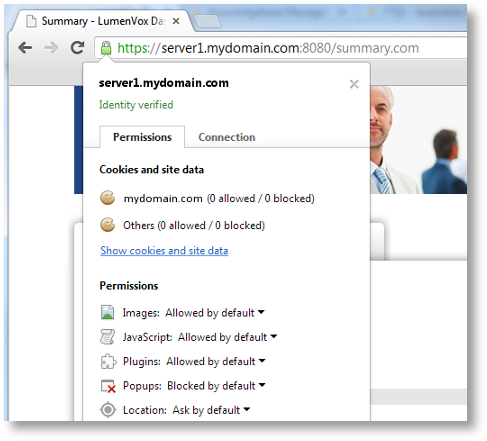
Once a valid, authenticated certificate is installed, the errors should not appear, and should appear correctly in the browser, when clicking on the padlock symbol, as shown below
Authenticated Certificate (for fictitious server1.mydomain.com):
New in 15.0.100
SSL Protocol and Cipher Selection
Prior to version 15.0, the SSL Protocol and Cipher selection was automatically performed and allowed the use of SSLv2/SSLv3 protocols, which are no longer deemed secure.
Introduced in LumenVox version 15.0 were a set of changes that affect HTTPS connectivity to the Dashboard. Specifically, SSLv2 and SSLv3 protocols are no longer supported. The default protocol is now TLSv1.2, with the option to allow the user to select TLSv1.1 or TLSv1.0 if desired, using the new SSL_PROTOCOL setting in the manager.conf file. These changes also included a modification to the default certificate shipped with LumenVox products to use a stronger cipher when the certificate is created (prior to shipment) - this change involved moving away from the SHA1 1024-bit algorithm to instead using a more secure SHA256 2048-bit algorithm.
Also as part of the changes introduced in LumenVox version 15.0 was a new configuration option CIPHER_LIST, which allows advanced users to specify which SSL ciphers can be used as part of the HTTPS exchange when connecting to the manager/dashboard.
The combination of these changes, along with internal changes to use the latest version of openssl significantly improves overall connection security. Note that on Linux systems, the version of openssl that will be used by LumenVox services is determined by the version that is resident on the system, so users are encouraged to update their versions of openssl and associated modules regularly to address any potential vulnerabilities that are identified over time.
Further Reading
For more information relating SSL certificates, and how these are used, there are a number of sites online that can provide this information, such as: